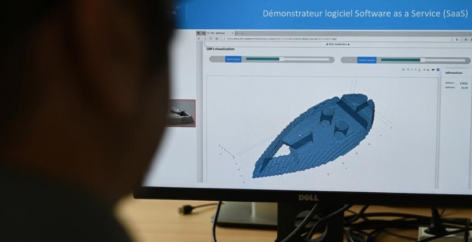
Demonstrate the resilience of mobility services on a real vehicle
For the first time in the academic and industrial community of autonomous mobility, solutions for detecting malicious activity in application data transmitted via V2X (Vehicle-to-Everything) technology have been demonstrated both on a real vehicle platform and on a simulation platform. Developed by IRT SystemX in collaboration with Renault Ampere, Eviden, and Trialog, these innovations aim to optimize attack detection and to alert the security system in real time, making mobility applications safer, more robust, and more resilient to attacks.
Published on 09/15/2025
 Autonomous, connected, and cooperative mobility services (CCAM: Connected, Cooperative & Automated Mobility) rely on V2X data sharing between various communicating entities. To ensure a robust and high-quality service, trust in the exchanged data (integrity and authenticity) and the entities generating them is essential.
Autonomous, connected, and cooperative mobility services (CCAM: Connected, Cooperative & Automated Mobility) rely on V2X data sharing between various communicating entities. To ensure a robust and high-quality service, trust in the exchanged data (integrity and authenticity) and the entities generating them is essential.
The solutions developed by the teams at IRT SystemX and their partners leverage several technologies and methods: misbehavior detection, models for verifying the plausibility and consistency of collected data, and more advanced data fusion techniques such as subjective logic (a formalism based on evidence theory). The work carried out has enabled:
- The development of a misbehavior detection module and its evaluation under realistic simulated attack conditions (F2MD2) as well as real on-road conditions (thanks to the institute’s automotive platform).
- Active contribution to European standardization communities, notably ETSI.
- Raising awareness within academic and industrial communities about the challenges posed by attacks on V2X data.
In the coming years, the module will be improved and tested within more advanced architectures based on edge computing technologies (an optimization method used in cloud computing that processes data at the network edge, close to the data source).
Key figures:
- 9 scientific publications
- 1 ETSI standardization on misbehavior reports